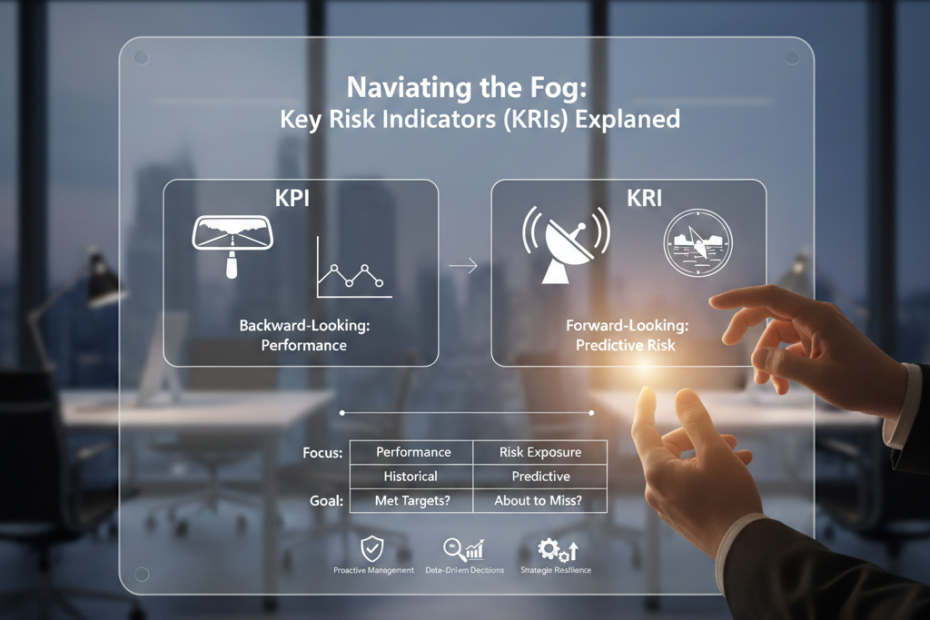
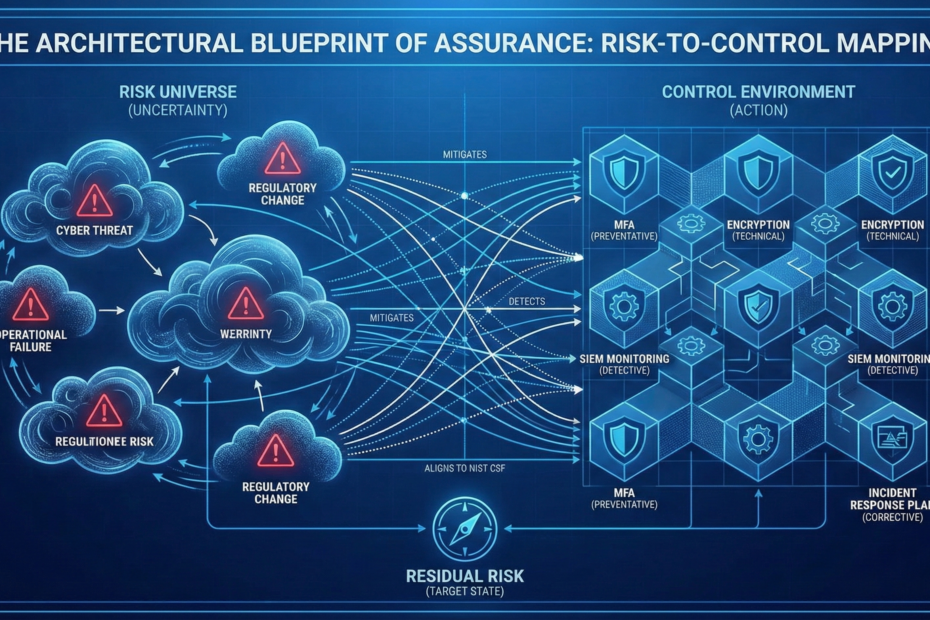
Vendor Risk Assessments: Best Practices
In today’s interconnected digital ecosystem, your security perimeter no longer ends at your firewall. It extends to your cloud providers, your payroll processors, and every third-party integration in your stack. With supply chain attacks on… Vendor Risk Assessments: Best Practices